Anvil e-signatures are “digital signatures,” meaning it uses cryptography to sign and fingerprint the documents as each signer adds their signature. That way, you can be assured any Anvil signed documents have not been tampered with after the signing process. When you sign a document with Anvil, you are kicking off a very complex process that includes several algorithms and authorizing parties.
In short summary, document signing works as follows:
- The process begins by hashing the entire document to create a digest.
- That hash is then encrypted with a private key that is linked to the requestor (i.e. Anvil) by an approved Certificate Authority and embeds that private certificate into the PDF.
- The PDF now has the raw signature data along with the encrypted hash created earlier.
- To verify this signature, you need to decrypt the hashed signature and take the hash of the raw signature. Those two hashes should match, verifying that the signature is valid and untampered with.
- This verification process is done behind the scenes when the PDF is opened using a PDF viewer like Adobe Acrobat. Adobe also has a list of approved certificate authorities it will verify the private certificate against.
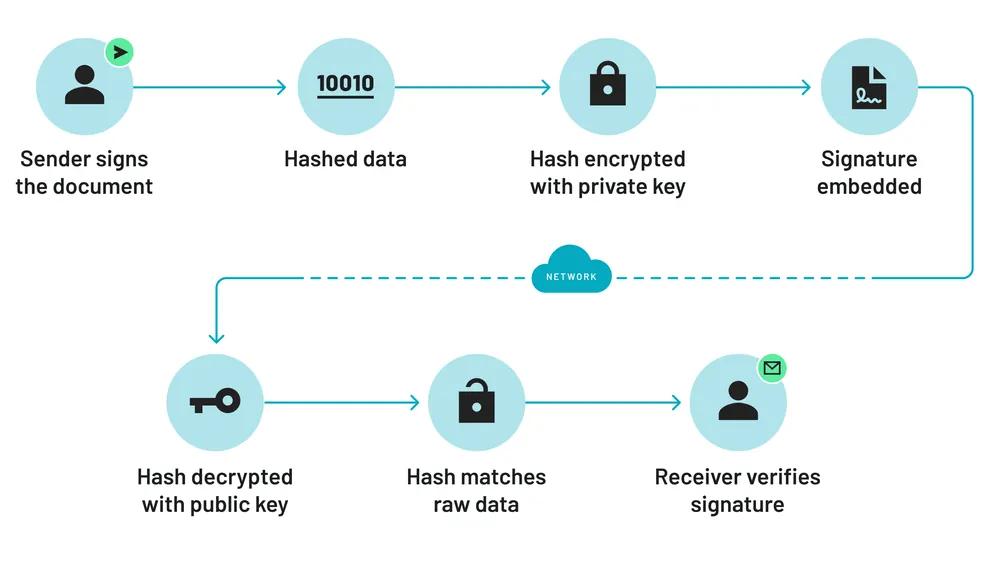
This is a very general overview but you can learn more about the signing process by reading about each piece individually.
Four components of a secure digital signature process
1. Document Signing Certificate
Anvil's e-signature API solution uses cryptographic keys to sign documents at each signature step. Cryptography is very secure, but you can't just take someone's word that keys are secure. That's why there should always be a guarantor, known as a Certificate Authority (CA). A CA validates that the keys were created by the right person and that the people who created the key are who they say they are. The CA gives a stamp of approval on any certificate made with an approved key. This stamp of approval says "I have verified this person's identity, they are who they say they are, and the private key they are using is valid".
The whole digital signature process hinges on the document signing keys issued by the Certificate Authority. Public Key Infrastructure (PKI) then uses the keys issued to sign the documents.
2. Public Key Infrastructure (PKI)
Public Key Infrastructure is a common practice used for authentication. This procedure requires that two keys exist, a public and a private. Anvil’s document signing keys are created by the Certificate Authority mentioned in the last section.
Think of the private key as a lock and the public key as a key. There are several copies of the public key, everyone can have one. But if someone was impersonating me, the public key would not work on their lock. The only lock that can be opened by that public key is in the possession of the creator of that key. PKI is commonly used for authentication - HTTPS (TLS) for websites uses the same system.
Signatures must be secure, e-sign laws around the world have extra requirements in how document signing private keys must be stored. Digital signatures are the most secure form of electronic signatures because they require certificates to be issued by an approved and trusted Certificate Authority (CA). This CA must authenticate the identity of the requestor (Anvil in this case) via multiple measures such as address, phone number, physical identification, and other procedures. They will also validate that the private keys are securely stored in a hardware security module. Once all of that has been validated, only then will they issue a certificate binding the private key to the requestor.
3. Hardware Security Module (HSM)
A Hardware Security Module is tamper resistant hardware devices used to generate and store keys. These are so secure that once a key is created there is no way to access it. These modules are tested and certified at the FIPS 140-2 standard and are virtually impossible to breach.
Nobody can access these keys! Not developers, not the creator of the key, not the storage center, no one at all. The HSM is a vault that doesn't open, it just tells you if the key fits or doesn't fit. You can never actually see what's inside.
4. Hashes
The goal of a hash is straight forward, to create a fixed length string that is always the same if the data presented to it is the same. Some examples of hashing algorithms are MD5 and SHA256. The idea is that if you have some data and run a hashing algorithm, then someone on the other side of the world with the same data should get the same exact hash from that data.
The hashes are how we verify that a document is identical and has not been tampered with. If a document has not changed after signature, hashing its contents will produce the same hash for everyone everywhere. PDF readers use this information to verify that a signed document has valid, untampered signatures, often showing a green check mark to indicate a document has valid signatures.
If a document is changed after signature, even by a single letter, it will generate a vastly different hash than the hash stored in the signed document. If the hashes are different a document has been tampered with post-signature.
Anvil: Ensuring security in every digital signature process
Digital signatures provide unmatched security and peace of mind, ensuring that signed documents remain tamper-proof. By utilizing advanced encryption, certificate authorities, and hardware security modules, platforms like Anvil offer businesses a reliable way to authenticate signatures and protect their data
If you're ready to get started, see how Anvil Document AI can speed up your document workflow processes.

